| This document is available in: English Castellano Deutsch Francais Nederlands Russian Turkce |
![[Photo of the Author]](../../common/images/Georges-Tarbouriech.jpg)
by Georges Tarbouriech About the author: Georges is a long time Unix user (commercial and free). He is
very interested in free security tools and really appreciates their
high quality. Content: |
![[article illustration]](../../common/images/illustration180.gif)
Abstract:
Security has always been one of the main concerns for sysadmins.
However, because of the Internet "explosion" the risk of intrusion
became even much higher. Statistically, if the number of connected
users increases, the number of crackers follows the same growth.
Accordingly, the development of security software grew up
exponentially. Once again, thanks to the free software community,
since it provided us with the best tools ever seen and with a lot
of documentation.
You'll find many interesting links in the reference section at the
end of this article. Obviously, what we will mention here can't be
exhaustive. I present just a selection of good tools.
This article is intended for private users as well as for
sysadmins, since some tools are designed for hosts protection and
others for improving network security.
Most of these tools work on many Unix flavors (if not all), whether
these Unixes are commercial or free. Last, this article is not a
"How to secure your network or your machine" but a presentation of
various tools you can (must) use to improve the security of a
network or a machine.
Let's call this section "tools for whitehats to protect redhat
from blackhats" :-) Most of the Linux distributions (not only
RedHat!) come with a lot of good security tools. They can be used
to make your machine more secure.
Among them we can mention TCPWrapper, PAM (Pluggable Authentication
Modules), shadow utilities... Since they are part of distributions
you'll find a lot to read about them : HOWTO, man pages, so we
won't spend too much time on them.
Let's start with the shadow utils. To make it
short, they allow password encryption. The /etc/passwd file is
replaced with /etc/shadow.
Something much more elaborated is PAM. As the name
says, it's another authentication method. It is used to configure
access to services. A lot of restrictions can be defined from some
configuration files thus making administration easier. Usually
those files are found in the /etc/pam.d directory.
TCPWrapper, it's enough to say that it allows to
restrict service access by IP address or hostname. They can be
allowed or denied via two files : /etc/hosts.allow and
/etc/hosts.deny.
TCPWrapper can be configured in two different ways : either moving
the daemons or modifying the /etc/inetd.conf file. If TCPWrapper is
not part of your Unix flavor, you can get it from ftp://ftp.porcupine.org/pub/security
And now, you will understand why we didn't say much about the above
mentioned tools : a single tool can manage all that for you while
teaching you. The one and lonely Bastille-Linux.
If you only install one tool, this is the one! It is not (yet?)
part of the normal Linux distributions but you can get it from http://bastille-linux.sourceforge.net
By the way, we will say nothing about Bastille-Linux!!! It's
useless, since there's an excellent article about it in the
September LinuxFocus issue from my fellow Frédéric :
he tells you everything. If you don't have read it yet, just have a
look there.
Let's add Bastille-Linux is a tool you can't live without!
Another generic tool to improve security is called
xinetd. It's available from http://www.xinetd.org. Sorry, but we
won't talk about it, neither!!! Once again, Frédéric
has done the whole job in the November issue of LinuxFocus. You can
read it here.
That was FredFocus section...
Don't worry about the money Fred, I can wait...
Now, let's have a look at some specific tools.
Free Unixes come with software to make your machine act as a
firewall. The 2.2 kernel provides you with
ipchains. Previous 2.0 kernel used
ipfwadm. To get ipchains or ipfwadm to work, the
kernel must be compiled with the right options. A lot of
documentation is available on the matter through HOWTOs, then,
again, we won't say more about it.
In short, let's say a firewall is a packet filtering tool. The most
important part of the work concerns the configuration of the
firewall. That is, a bad configured firewall can become very
dangerous.
Nevertheless, firewalls are important.
For instance, Bastille-Linux provides you with a firewall based on
ipchains.
If you go to http://www.linuxapps.com and type
"firewall" in the search field, you'll get at least 40 answers.
Many of them are GUIs for ipchains or ipfwadm administration. Some
others are really big tools with tons of features, like T.REX for
instance, available from http://www.opensourcefirewall.com.
Again, don't be fooled : a firewall is compulsory on a network, but
the network security cannot ONLY rely on it. A cracker may break it
in about 15 minutes! You've been warned.
Here we reach the heart of the problem. The idea is : use the
same tools as the crackers do, to check the vulnerabilities of your
network (or machine).
In this area we can benefit from two very great tools but there are
many others.
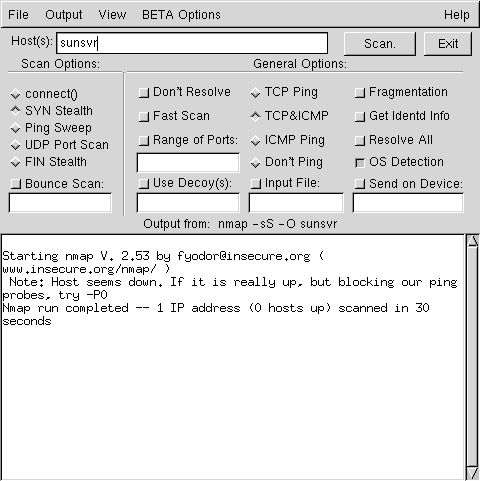
The first one is called nmap. You can download
nmap from http://www.insecure.org. Even more,
you'll find there a lot of information, links...
With nmap you can check which ports are open on a machine on your
network. Sure, you can do that with commands such as lsof or
netstat but only for your own machine. Obviously, you can check
your own machine with nmap.
nmap can provide you with a lot of information : for instance, it
may tell you which OS is running, inform you about dangerous open
ports... Last, but not least, nmap is quite easy to use.
nmap can be used either from a shell or from a graphical interface
called nmapfe. The GUI is based on the gtk lib. The present version
of nmap is 2.53. It works on many Unix flavors and is available as
source code, rpm, with or without GUI.
nmap is the tool sysadmins cannot live without!
Many thanks Mr. Fyodor and congratulations for this great job.
The second one is called nessus. It can be
downloaded from http://www.nessus.org . Nessus works
according to the client/server architecture and the Posix source
code is usable on many Unix flavors. There's even a client for
Win32 (just to let you know).
Nessus relies on nmap (you see you can't do without!) and the gtk
lib for its GUI.
Present version is 1.06 and with it you can scan a whole network in
one command, that is the network address. For example, typing the
address 192.168.1.0/24 in the target field will scan the 255
machines from that network.
Even if nessus is a bit more complex than nmap, it's still easy to
use and has a lot of features. For example it can generate reports,
it can make diffs between reports... Another feature is quite
interesting : nessus suggests solutions to the problems found
during a portscan. As soon as the machines are Unix machines, the
suggestions are often good ones. They will be less appropriate for
others OSes. Anyway, that's not the point.
Here is an example from a very vulnerable machine:
Nessus has another great feature : it works with plugins, it can
easily be updated each time a new security hole has been found
somewhere.
Another tool sysadmins do need! Great job Mr. Deraison and "Merci
beaucoup".
Both tools have been tested from a Linux box on a network with
different OSes : Linux RH 6.2, Irix 6.5.7, Solaris 2.6, NeXTStep
3.3, QNX RT, BeOS 5.0, Amiga OS 3.5, Not Terminated 4.0. The
results are impressive for most of the platforms. Of course the
Amiga OS is not really well identified (since it appears as a
printer or a router!) but who has still this OS in a network (apart
from me)?
Anyway, these tools are a "must have" in today's networking.
To end with this chapter, let's mention some other tools such as
SARA http://www-arc.com/sara/, or its
"father" SATAN http://www.porcupine.org/satan/,
or SAINT http://www.wwdsi.com.
They are not only port scanners and they can be quite useful to
improve network security.
Some tools are able to detect portscans or intrusion. A
"standard" (that is paranoid!) sysadmin CANNOT work without this
sort of tools.
The first suite of tools comes from the Abacus
Project. You can get these tools from http://www.psionic.com. Three
different tools are available : logcheck, portsentry and
hostsentry.
Logcheck is in version 1.1.1, portsentry is in version 1.0 and
hostsentry is in version 0.0.2 alpha.
Portsentry is a portscan detection tool. As its
name says, if a port is scanned from somewhere, portsentry will
immediately block the host, either dropping the route using the
firewall (or an unused IP address) or writing the IP address of the
attacker in the /etc/hosts.deny file as soon as TCPWrapper is
installed on your machine. The result is quite efficient!
Porsentry relies on a main configuration file and on a few specific
files. The later are used to ignore hosts (that is not to block
them) or to block some port on some host.
From the config file, you define the way portsentry will work.
You'll first select the ports you want to bind to portsentry,
either TCP or UDP ports (or both). Be careful with port 6000
binding if you run X11!
According to the Unix system you use, you can have two different
modes of operation to monitor the ports. The advanced mode is only
available for Linux at the moment.
Next you select the blocking option : either you don't block the
scans, or you do, or you may run an external command.
You then choose the way to drop the route, either redirecting the
attacker to an unused IP address from your network or to a packet
filtering (firewall).
The following step concerns TCPWrappers. That is you decide (or
not) to write a DENY text in the /etc/hosts.deny file.
Next you can define an external command to run and last, you may
select a trigger value for the scan (default to 0).
That's all you have to do! We suppose you know everything about
logging, since, obviously, all the alarms are logged. That means,
you can modify your syslog.conf file if you want the eventual
alarms to go somewhere else than /var/log/messages or
var/log/syslog or /var/adm/messages...
You now can run portsentry in the background with the option of
your choice. The available options depend on your system : you'll
be able to use -tcp, -udp on most Unixes and -atcp, -audp on Linux
boxes ("a" for advanced).
Let's have a look at the result when scanning a machine where
portsentry is running.
Here, we can't talk about tools. Scripting is one of the main
skills of any sysadmin. Shell scripts, Perl scripts... are part of
your everyday's job if you are managing networks.
Obviously, scripts can be used for automating tasks, but as well
for security monitoring. Every sysadmin has his own needs and he
always tries to manage them in the way that suits him. It is not
always so easy. Something can help : subscribe to SysAdmin
magazine! This magazine is made by sysadmins for sysadmins and
provides you with a lot of programs, scripts... You can even get a
CDRom containing all previous issues, and of course all previous
programs or scripts.
This is not advertising... it's a way to find more solutions to
improve security. Go and have a look at http://www.samag.com.
If you are a sysadmin, let's say you should give it a try.
Well, it's only a suggestion.
There is much more to add about security, but as we said before,
this article is not a "How to secure you network". A book on the
subject wouldn't be enough. Security doesn't only rely on tools, it
is also a behavior (sort of). For instance, some common behaviors
make me mad. When will people understand that M$ Office files are
just like bombs? They are not only "enormous" in size, but
potentially full of macroviruses. Please, Wintel users, DO NOT SEND
Word or Excel documents as mail attachments. Furthermore, if you
receive some of them DO NOT OPEN them : this is only a suggestion,
but you have been warned! They are as dangerous (I should say
more!) as any executable you receive (or download). And, by the
way, plain text or HTML files are much smaller in size than Office
documents, and they are NOT dangerous!
Of course, I know the Wintel word works this way : when you
download a single driver, it's always an executable! Let's admit,
we can trust the big firms... but do you know what could have
happened to the archive you download? Sure, it's a paranoid way of
thinking, but is it so crazy? Why do you think many archives have a
checksum to verify authenticity?
The following may "hurt" many people, but it's a fact : JAVA is
dangerous! Applets are insecure, Java scripts are insecure.
Nevertheless, it would be interesting to know how many websites use
Java! Furthermore, Java is a source of problems when visiting
websites : how many of them will freeze your browser? Is that the
goal of a website?
Don't we talk about ActiveX from the Redmond army!
Suggestion : use Rebol instead (http://www.rebol.com)
Since we are on the matter : please, new Internet "professionals",
stop creating websites dedicated to the Wintel word and IE5! I'm
aware these things are widespread, however many people connect to
the Internet with many different OSes and many different browsers.
Working the way you do, prevents people from visiting your website.
The aim of the Internet is to share. Using proprietary things is a
nonsense. In my humble opinion, when making a website, the first
thing to do is to check it from different OSes and different
browsers... but this is only my opinion. Just for information : if
you connect to such a website with an Unix machine and let's say
Netscape, you can't even view the index page!
Sorry for the digression.
Another important point is to remember that security won't reach
100%. We are far from it. You can improve it, that's all : it's a
fact. For example, you can use all the tools we mentioned here and
leave a back door wide open! Don't be fooled : crackers won't try
to break a 128 bit key at first, but they will try to find a small
hole somewhere. So be careful with SUID or SGID programs, with
access rights, with useless running services, with canceled
accounts and so on.
If the different Unix flavors have many similarities, they are much
different concerning security. Some of them are just like sieves!
You must be aware of that too. For instance, having an Internet
cable connection with a standard Winsomething machine is great :
that is, you can have the icon of the cracker's machine in the
network neighbourhood... and soon M$ will provide you with the
picture of the cracker! I'm only kidding...
The road to networks and computers security is a very long one. If
you are interested in this matter you will learn everyday.
Fortunately, there are a lot of sources to get information. Here
are some of them.
http://www.linuxsecurity.com is
the first gold mine. There you'll find almost everything!
http://www.sans.org is the place
to get help and information about security. A site you should
consult on a regular basis.
http://www.infosyssec.org
is another place to get tons of information about security.
http://www.securityfocus.com is
the home of Bugtraq thus providing lot of security information.
http://www.cs.purdue.edu/coast/hotlist/
THE site you must visit!
Going to the top of this page you'll find a "Links" button : click
on it to get the addresses of most of the distributors. Consulting
their site is compulsory to get information about security patches.
This applies to every Unix editor! Many of them release security or
recommended patches on a regular basis.
Many articles in previous LinuxFocus issues are worth reading
(apart from the already mentioned):
Adding Security to Common
Linux Distributions
TCPD and Firewalls using
IPFWADM
VXE, a Linux security
tool
Many more documentation is available and we can't provide all
the existing links. Neither can't we mention all the free security
tools as already said. From every site mentioned here, you'll find
more links sending you to even more links, and so on... just like
Russian dolls.
The fact some tools or sites are not present in this article
doesn't mean they are of no interest. It only means the tools have
not been tested by me. Obviously, you have to make an arbitrary
selection among the hundreds of available tools.
The goal of this article is to provide the readers with places to
start from. We hope it'll help.
|
|
Webpages maintained by the LinuxFocus Editor team
© Georges Tarbouriech, FDL LinuxFocus.org Click here to report a fault or send a comment to LinuxFocus |
2001-01-27, generated by lfparser version 2.8